
As we all become more connected, we are gifting platforms with our personal data, that they farm for capitalist ambitions, while totalitarian regimes create a surveillance world to encourage conformity and reward, or more worrying, non-conformity to persecution and punishment.
During the 1980s, I was sent to the Soviet Union to negotiate a joint venture deal between several Government Ministries and a leading telecom provider.
What confronted me was like a scene from George Orwell’s classic novel Nineteen Eighty-Four: A society of educated but suppressed people. The State controlled every facet of daily life. Most prominent was the grey and decrepit backdrop of a community under constant surveillance; the crumbling regime’s ubiquitous eye demanded compliance to a broken government system fuelled by strident propaganda that increasingly lacked any resonance with the general population.
For the majority, life was made miserable by the social networks that fed the suppression machine.

Absolute Surveillance of Action & Thought
In Orwell’s ‘1984’, Winston Smith (6079 Smith W.) contends with Oceania and Big Brother’s absolute surveillance of action and thought. As he stood in front of his telescreen, he realises with terror that he is under surveillance.

The Soviet Union could not build the capabilities of an all-seeing, ever-present telescreen. That task was left to the most liberal society on earth, Northern California, with the best intention of enhancing humanity through the connectivity of individual citizens. Concepts like social media and the democratisation of content were born. Now it was cool to share every facet of one’s life, no matter how puerile.
![]()
A Perfect Honey Trap
The concept of the ‘Selfie’ was borrowed straight from the pool of Narcissus. Instead of taking pictures of others, the photographers fell in love with themselves.
The Selfie became the primary fuel of new sharing platforms, particularly for the young, who become equipped with devices and connectivity contracts.
Everyone became connected and started to share what they thought would feed their sense of well-being. Those gifting the platforms were now farming any personal data they thought helpful in monetising their monopolist ambitions. In the background, totalitarian regimes became empowered to create enfranchisement systems through surveillance that could link conformity to reward, or more worrying, non-conformity to persecution and punishment.
The technology community had created a perfect honey trap but curiously were left by governments to run rampant over privacy issues and concerns. Historically, the providers of national and regional telecommunication networks were heavily regulated to ensure citizens were protected from both commercial and State interception.
A warrant from an independent member of the judiciary and a Government Minister must approve any such intrusion on the telephone network (the Double Lock principle). However, the Internet’s over-the-top services were granted total immunity from regulatory frameworks necessary to protect the public from abuse. The regulators and politicians were left bewildered at the pace of innovation and adoption. Many suppliers of these data harvesting platforms also fed the State surveillance apparatus, so had Governments bound into a mephistophelian deal, enabling their activities to continue unabated.
Like numerous roads to hell, they were paved with good intention: The lofty aspirations sounded splendid around the corridors of power:
“Let’s connect all humanity”, “we will lower the barriers of learning and understanding”, and what’s more, “we can do it at no cost to the user.”
It sounds beguiling because it is, but sadly there is a high cost to the participant. Not only are people being farmed by the surveillance capitalists, but they are also easy prey for the instruments of State, both foreign and domestic, to manipulate and monitor their behaviour.
The rampant consumerism of society provides endless opportunities to embed capabilities to put people under further surveillance. Any electrical device from the obvious (cameras, computers, phones and wearable devices) to the less prominent (environmental systems and children’s toys) provide a cornucopia of surveillance means to feed the machine. Winston Smith needed to avoid the telescreen; who knows where the new ‘telescreens’ are embedded in our living and workspaces?
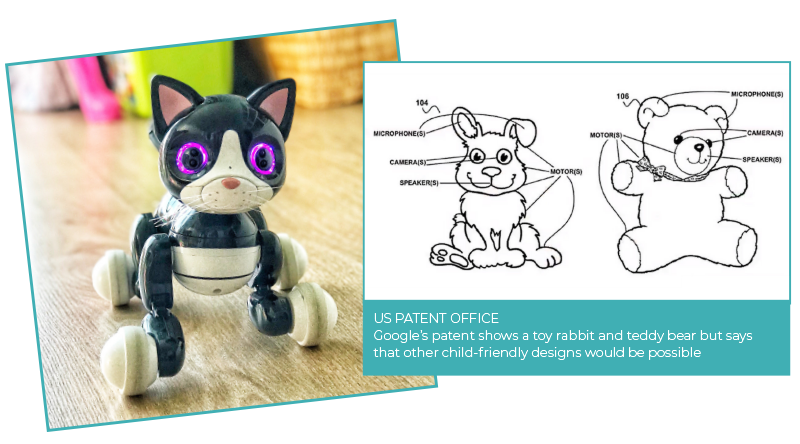
In most developed democracies, the population is fortunate to have government agencies that are required to behave responsibly in the realms of surveillance. There are strict laws that protect people from the abuse of privacy. However, the events of the last decade have demonstrated the ‘watchers’ need watching. In the UK, that role is fulfilled by an Intelligence Service Commissioner alongside the judiciary and ministers. However, vast swathes of the world’s population do not enjoy such protections. They are easy pickings to those who use networks, computing devices and software to monitor, steal, extort and abuse. Crime syndicates, hostile states, or rogue hackers attempt to wreak havoc on all society’s structures; their purposes include destabilising economies, encouraging conflict, and poisoning the minds of the innocent.
A Gunfight with a Pocketknife

The asymmetric nature of this growing conflict is a challenge for functioning democracies. On the one hand, they have offensive and defensive cyber capabilities but are expected to act with appropriate restrictions by the society they are employed to protect. On the flip side, the enemy can attack in any way they choose, at any time and by any means. It is akin to going to a gunfight with a pocketknife. This dilemma is expressed in the following excerpt for the UK’s Integrated Review of Security, Defence, Development and Foreign Policy, 2021:
Companies and citizens are restricted to only utilising defensive strategies, which are in nearly all cases reactive. Any engagement in offensive attacks without Government consent is outlawed. The US second amendment curiously allows the citizenship to bear arms and use them when attacked for lethal means, but in Cyberspace, any unauthorised retaliatory attack would be considered a criminal act.
Digital Defenses

By its very nature, it is often a challenge to observe the covert behaviour of national States, but when they do come to light, they attract international headlines. The bigger problem affecting millions of people and businesses every day is from cybercriminals and hackers operating in jurisdictions that are happy to let the perpetrators wreak havoc, so long as they create detrimental outcomes to competitive nations. These hackers create offensive campaigns requiring rapid detection. Timely countermeasures need to be implemented to shut this activity down, and in these instances, speed is vital. Domain Name Servers need enhanced intelligence, and firewalls need to know what to block. Waiting for updates every week or so leaves the network in a vulnerable state. Solutions are required to understand and pre-empt the attack at the source and inform the network of the miscreants’ actions.
The criminal fraternity understands that more than 90% of security breaches are caused by human error. The methods of social engineering are becoming more sophisticated and presented through multiple device types. Cyber awareness training with tracking and testing is the only way to keep ahead of the threat. It can never be a one-off event as criminals will never stop innovating in the art of deception. Evidence suggests continuous education is proven to result in a more informed and protected society and workforce.
If the perpetrators successfully farm sensitive data, their next step is often to find buyers for the information. These trades are invariably undertaken on the dark web. Bank account detail, logins, passwords and Intellectual Property are all offered for sale. Having the tools to track this activity, target offenders and locate them through an accurate understanding of network infrastructure and spectrum is a key advantage.
When you consider the ethics of surveillance and the cyber activity of governments, companies, criminals and hackers, you quickly realise the dichotomy between offensive and defensive strategies is complex. On the one hand there is a clear need to go on the offensive to fight criminal and hostile nations attempts to destroy the fabric of Society, but to do so in the constraints of a legal framework that protects a democracy is a predicament. It is imperative that the regulatory frameworks catch up with the realities of the technology.
The Good Verses Evil Dichotomy
In every great breakthrough in science, there are always those who seize the opportunity to deploy it against the good of humankind. Examples include nuclear energy, quantum, biological and chemical compounds, aviation and space. In the world of computing and the internet, which is still in its relative infancy, there is the same trait manifest in every new innovation. The classical good and evil dichotomy is pulsing through our digital structures.

In this continuing cyber chaos, maintaining safe and secure spaces for economies and societies to trade and share values will continue to be an expensive and complex necessity. The full extent of that effort and cost is increasingly being recognised across commerce and governments.
There is a growing perception in the accelerating advance of knowledge that mankind can do anything. In the wake of these new found powers is a vacuum that can be filled by asking “what should we do”. A candid and truthful debate on the relevance of digital privacy rights and surveillance intrusion is arguably long overdue. With the vested interests of the capitalist and nationalist tribes, the welfare of society continues to be pushed into the shadows.
The relentless offensive cyber-attacks in all their guises will only intensify. Support should be afforded innovators, leaders and regulators who choose to devote their efforts to protect society from the surging trend towards total transparency in the human experience achieved through total surveillance.
In Orwell’s ‘1984’ narrative, eventually, Winston Smith accepts he loves Big Brother. He is taken to Room 101 and forced to confront his greatest fear; a cage of frenzied rats in his face and immediately surrenders to the interrogators. Oceania broke his spirit to fully comply with the demands of ‘Doublethink’. Through our insatiable appetite for connectivity and convenience, have we become conditioned to end up like Winston, or would we find our worst fears around institutional and corporate surveillance and intrusion alive and well in Room 101?
© Copyright Simon J. Gibson
